Make Security Great Again Not by Building Firewalls
Abstract
The purpose of this white paper is to discuss the development of network security and what it will take to protect an organization's environment for the time to come.
As networks become more than heterogeneous, it becomes increasingly difficult for organizations to achieve consistent policy management and enforcement and maintain unified visibility. The complexity of these interconnected networks ofttimes leads to errors or misconfigurations, leaving them vulnerable to e'er-evolving, sophisticated threats.
What can an system practise to regain control and accomplish consistency? Information technology starts with an integrated approach to security that places the firewall front and center.
Firewalls are still the cornerstone of an organization's network security strategy, but merely as networks have evolved, so also must our firewalls. In the by, the firewall was a single apparatus at the ingress/egress "perimeter" interim as a policy-driven control point to allow or deny network traffic. To succeed in today's digital globe, organizations need to think beyond single firewalls and embrace "firewalling"— a policy-driven method for strategically analogous avant-garde security protections across logical command points throughout heterogenous networks.

Firewalling will be a critical stride for organizations to ameliorate align security with irresolute business and networking needs. Cisco has been hard at work building an integrated security platform with our firewall at the foundation to enable businesses to make the transition.
With firewalling, organizations that are digitally transforming can achieve a stronger security posture today while building a span to come across tomorrow's business and security demands.
Section 1: The history of the firewall
The evolution of network security
Traditionally, the firewall was placed as a gatekeeper on the network edge. It acted as an all-encompassing command betoken, inspecting network traffic as it traveled across this perimeter. Sitting at the network'southward ingress/egress point, the firewall was responsible for validating communications: internal network traffic was considered inherently trustworthy, and external traffic was considered inherently untrustworthy. Rule sets and policies were created and enforced at this single point of control to ensure that desired traffic was allowed into and out of the network and undesirable traffic was prevented.
Comparison the network perimeter to a moat around a castle, the firewall acted as a drawbridge controlling all traffic in and out of the fortress.
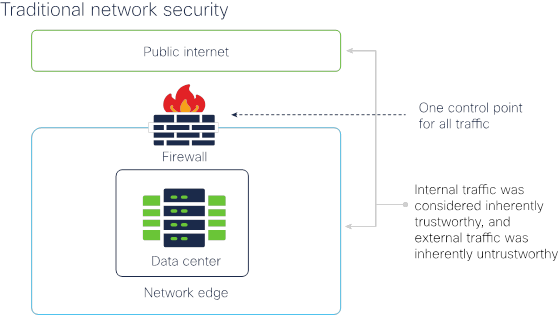
Effigy ane. Traditional network firewall approach
Forth came the cloud. And apps.
It wasn't long before this practise of enforcing security through a unmarried control signal was challenged. Commencement, there was the ascension of remote access and enterprise mobility. Only transformation really kicked in with deject calculating. When business moved to the cloud, devices and users began migrating en masse outside of the controlled internal network, which made the single control betoken model ineffective. Shortly, in that location were multiple perimeters. They all needed to be secured. At that place was no effective manner to put one moat around the network.
Today, branch function locations, remote employees, and increasing use of cloud services are driving more than data abroad from the traditional "perimeter," bypassing the traditional security control point completely. Additionally, many businesses have adopted a bring your ain device (BYOD) model, allowing employees to access sensitive business applications through their private computers or mobile devices. In fact, more than 67% of employees use their own devices at work - an upward trend with no end in sight . Mobile devices and laptops connected via publicly accessible Wi-Fi networks are prevalent, even crucial for day-to-mean solar day business organization operations.
Further, the overwhelming bulk of concern locations and users also require straight admission to the Internet where an increasing majority of cloud-based critical applications and information now live. Businesses keep to deploy workloads beyond multiple cloud services, operating systems, hardware appliances, databases, and more. Applications and data become further de-centralized, and networks subsequently become more diverse.
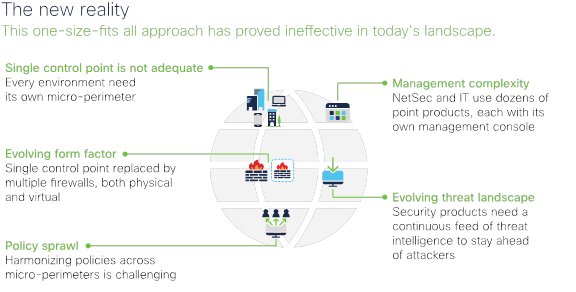
A new, more complex reality
While these innovations allow for a more interconnected and productive work surroundings, they've changed the very nature of the way we practise business. The days of controlling applications and authorizing users on-premises have morphed into dynamic, multicloud ecosystems delivering services and applications across enterprises. Not only that, we're also managing business-disquisitional third-party relationships. Vast expansion and outsourcing provide economies of scale and efficiency, merely not without tradeoffs. This evolution of network architectures has profoundly increased our attack surfaces and made the job of protecting business organisation networks, data, and users strikingly more complicated.
Fighting back with point products
Typically, organizations have attempted to accost these challenges past calculation the "best" point security solution to address each new problem every bit it emerged. Because of this approach, nosotros have seen tremendous device "sprawl," with the boilerplate enterprise using upwards to 75 security tools1. Multiple security products across different vendors tin pose pregnant management problems for network security teams.
1 "Defense in depth: Stop spending, start consolidating," CSO, March iv, 2016.
ii "Navigating Network Security Complication," ESG Research Insights Report, June 2019.
3 "Navigating Network Security Complication," ESG Research Insights Study, June 2019.
In most cases, a proliferation of security devices and capabilities leads to an increase in the risk of attack. When asked, 94% of It and infosec professionals were concerned that increased network complexity makes them more vulnerable, and 88% want to make network security policy changes more than active2.
Between January and July of 2019, iii,800 information breaches were disclosed — a 54% surge over the first half of 2018iii. This steep climb is a testament to the progressively sophisticated methods bad actors are using to alienation networks. The growing rate of successful breaches is also an indication that traditional methods of network security are no longer standing upwards against modernistic threats.
More than threats, more noise, even more risk
Every bit malicious parties attack new vectors — from email to unvetted endpoints under BYOD policies, to web portals, and IoT devices, organizations are besides driven to endeavor whatsoever number of other approaches to protect themselves.
As discussed above, the trend of adding signal products doesn't better an organization'due south overall security posture. Quite the opposite. Information technology creates more "noise" for security teams to manage. While they struggle to keep their eyes peeled for inevitable new attacks and malware seeking to exploit any vulnerability (either known or unknown), this added complexity makes the job of creating, managing, and enforcing security policies ever more than difficult.
In response, network security teams are tasked with configuring multitudes of deject resources individually, further increasing the chance of a security misconfiguration that could atomic number 82 to a alienation. A security command that's non implemented or implemented with errors can be the biggest culprit of all: 64% of organizations say that human fault was the leading cause of a misconfiguration4. Whether such a mistake leads to a violation of compliance, an outage, or opens the door to an adversary, it's run a risk you can't afford.
It's fourth dimension to rethink the firewall
Network security has get a daunting task. Today's personnel tin't proceed attempting to manage a mass assortment of bespeak security solutions, cloud resources, and appliances. It's time for a different approach.
Information technology's fourth dimension for the firewall to take its place as the foundation for an agile and integrated network security platform that volition pb to the for businesses of today and tomorrow.
Section ii: From firewall to firewalling
Why firewalling?
Equally our networks evolve to accommodate new ways of doing business, so too must our network security. In the current earth of distributed IT assets, the firewall is nonetheless central to a robust security posture.
However, firewall requirements take increased significantly to protect the wide array of network infrastructures, continued devices, and operating systems from advanced threats. Consequently, our "traditional" firewall devices are being augmented by a mixture of physical and virtual appliances—some are embedded into the network while others are delivered as a service, are host-based, or are included within public cloud environments. Some are even taking on new form factors, such every bit amassed appliances that calibration to large traffic requirements, software that runs on personal devices, SD-WAN routers, and secure Net gateways. The activity of sharing threat intelligence across all these disparate firewall devices, regardless of their location, is vital for uniform threat visibility and a strong security posture.
To make the full shift and better secure today's networks, businesses must movement away from the traditional "perimeter" approach. Instead they've got to found strategic enforcement points across the unabridged network fabric, closer to the information or applications that need to be protected. Specifically, the creation of micro-perimeters at both physical and logical points of control has become a necessary reality.
We need to think less about the firewall as a standalone physical network device and more than near the functionality of firewalling.
What is firewalling?
Make no error: the firewall is more relevant than ever. In fact, to secure today'southward networks we need more firewalls everywhere. The difference is that firewalling focuses on how you lot tin can establish policy-based controls everywhere:
Firewalling tin can provide an agile and integrated approach for centralizing policies, advanced security functionality, and consequent enforcement across your increasingly circuitous, heterogeneous networks. Information technology should deliver comprehensive protections, visibility, policy harmonization, and stronger user and device authentication. Firewalling should also benefit from the sharing of threat intelligence across all command points to constitute uniform threat visibility and control—dramatically cut the time and effort needed to notice, investigate, and remediate threats.
In this fashion, firewalling becomes a key strategy for securing your complex network today. And provides a bridge to the hereafter equally your business—and the threat mural—continues to evolve.
What is Firewalling?
Enforcement points are everywhere across today's heterogeneous networks.
Firewalling is delivering consistent threat prevention functionality with consistent policy and threat visibility so you can forestall, detect, and terminate attacks faster and more accurately, everywhere.
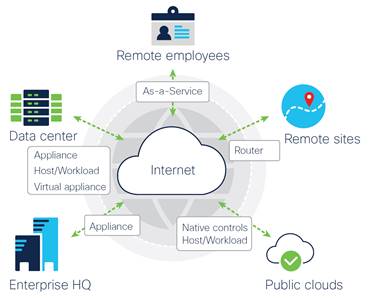
Figure 3. The core tenants of firewalling as a means to address the security challenges of modern networks
What does it look like?
Whether protecting avails and data in the deject, on premises, or at a remote location, firewalling needs to consistently provide advanced threat protections, policy enforcement, and shared threat intelligence. The challenge is delivering that consistency beyond disparate environments where dissimilar devices are deployed and utilized.
Security breaches tin can originate from whatsoever device that has access to the Internet, regardless of whether information technology'southward in the corporate headquarters, data center, remote sites, public clouds, or any location where an employee is working remotely. That's why it'south more important than ever to incorporate a robust set of security command points in more logical locations to reduce exposure and mitigate risks. Security controls are practical where needed on owned environments (physical or virtual appliances and network devices like routers) as well as non-endemic environments (Security as a Service [SECaaS]), native controls, and workloads.
Extending security controls
Under the premise of a traditional firewall, since all internal traffic and authorized users were inherently trustworthy (and external traffic wasn't), protecting the entire organization was accomplished at the network perimeter. This network perimeter became the logical security control betoken to protect the unabridged arrangement. All network traffic, whether originating from the headquarters, a data heart, or remote worker, was funneled through this single control indicate.
Of grade, this model does not work in today's complex environments where an organization'due south IT infrastructure spans a wide diversity of form factors and delivery models, including concrete and virtual appliances, network- embedded routers or switches, delivered as-a-service, host-based, or included with a public cloud.
With a firewalling approach, consistent security controls are deployed to provide full visibility, unified policy, and comprehensive threat visibility. These security controls enable stronger user and device authentication across increasingly heterogenous environments. They gather, share, and answer to context about users, locations, devices, and more to ensure devices meet defined security requirements. Using consistent security controls at every micro-perimeter, security teams tin outset to automate tasks (such as auto-quarantine out-of-compliance users and devices, block questionable domains across all security controls, and support effective microsegmentation). In firewalling, total visibility provides a holistic view of all security alerts and indicators of compromise, and shared threat intelligence delivers the near up-to-appointment threat detection to any continued device.
Cloud-based management
And it's non merely point products. The explosion of network perimeters and cloud resources has increased exposure for breaches as well. Safeguarding a business organization's most valuable assets in complex deject environments while managing various security products is no small task. Security teams need instant visibility and streamlined direction to aid reduce misconfiguration.
Firewalling promotes a stronger security posture past supporting centralized, deject-based direction to help security teams cutting through complexity and align policies throughout the organization. Templates can better policy design and consistency past writing a policy once and scaling its enforcement beyond tens of thousands ofsecurity controls throughout a network. The use of standard policy templates to rapidly deploy new devices helps reduce configuration errors. As organizations grow, new deployments automatically inherit the latest policies. A scalable policy direction system integrates multiple security features into a single access policy and optimizes policies beyond security devices to identify inconsistencies and speedily right them.
What's more, a centralized, deject-based management solution takes a team's capabilities to the next level. They tin quickly identify risks across all devices, bringing them to a more than consistent and secure state. With a single management console, objects tin be compared across all devices to uncover inconsistencies and optimize the current security posture. Personnel can streamline policy management, better efficiency, and attain more consequent security while reducing complexity.
Fighting back with threat intelligence
Equally the network perimeter expands and the number of devices directly connected to the Internet proliferates, our assault surfaces also expand. Cybersecurity threats involving malware, cryptocurrency, phishing, and botnet activity are escalating, and cybercriminals are turning to machine learning and AI to exploit existing software vulnerabilities and expedite malicious attacks. Very few organizations take adequate resources to fully exam and qualify all software vendor vulnerability patches – most are challenged to fend off the onslaught of emerging and evolving threats.
Another compelling aspect of firewalling can help here. Leveraging manufacture-leading threat intelligence with the latest threat research – some on a nearly upwards-to-the-minute basis – with access to protection updates helps mitigate the constant stream of threats. Threat researchers rapidly identify indicators of compromise and ostend and share threats quickly. Using economies of scale, they aim to protect organizations against developing threats before they happen. Sharing threat intelligence across interconnected networks, endpoints, workloads and deject environments helps security teams correlate seemingly disconnected events, eliminate noise, and terminate threats faster.
Firewalling begins and ends with the firewall as the cornerstone to future-proof network security
At Cisco, nosotros've been hard at work bringing this vision into reality. We piece of work with businesses and enterprises of all sizes across the globe, and all of them demand their network security to exist more active and more than integrated – baked into the network itself. That'southward why we're delivering the most secure architecture e'er, a powerful and comprehensive platform with the firewall as the foundation.
Providing an unprecedented level of protection through this concept is a major component of our security strategy. The Cisco security portfolio and Cisco's family of firewalls keep you i footstep ahead of evolving threats with globe-form security controls everywhere you demand them, consistent policy and visibility, and innovations that amend security operations.
In an era where the threat landscape is more dynamic than e'er before, Cisco brings networking leadership and cutting-edge engineering together then you can have the strongest security posture available today and tomorrow.
What are the risks of not firewalling?
Every bit networking has advanced, organizations have adjusted, deploying various point products to support business organization requirements and operations. They've done the same as new set on vectors are publicized, adding production afterward production to protect against the latest XYZ threat. Those that rely on a traditional firewall to secure every connected device across multiple perimeters risk exposing their most valuable data and assets to security breaches. Co-ordinate to the 2019 Cybersecurity Annual, cybercrime damages will cost the world $6 trillion annually by 20215.
These threats tin infiltrate a network speedily and jeopardize the operations of a business concern that lacks comprehensive network security and endpoint visibility.
That said, securing an organization's network, cloud environments, devices, and information wherever they are is a huge burden on security teams. Traditional firewalls provide a limited view; It needs greater visibility beyond the unabridged network with shared threat intelligence to notice and cake threats before and faster. Firewalling goes farther by delivering a comprehensive security posture based on unified direction and comprehensive security capabilities such equally intrusion prevention, URL filtering, and advanced malware protection leveraging automation and auto learning for efficiency.
Without a firewalling strategy in place, network complexity can lead to misconfigurations, escalating the risk for a security breach. According to a Gartner study, "through 2022, at least 95% of cloud security failures will exist the customer'southward mistake."6 By embracing a firewalling strategy of harmonizing security policies across multiple control points, organizations improve their overall security posture.
Department three: Four steps for setting upwardly your firewalling strategy
Step i: Set up the foundation for your successful firewalling strategy with a modernistic next-generation firewall. The right Cisco Secure Firewall will deliver consequent security policies, visibility, and improved threat response for your integrated security solution.
Step 2: Once yous've selected your Cisco Secure Firewall, the side by side pace is to standardize on a management solution. Consider these factors when determining which solution is right for your system:
● Determine the preferred direction location (on-premises, or cloud) and which group will be responsible for managing security (SecOps or NetOps).
● Nearly importantly, ensure the management solution aligns with Information technology's electric current and future goals. If y'all're moving workloads to the cloud, launching a vendor portal, or tackling digital transformation projects or SaaS applications you may want to prefer cloud-based direction. If your system relies on monolithic legacy applications, on-premise applications may adjust your needs. Generally, legacy applications have some re-factoring to run properly on the deject, and if there are no firsthand plans to upgrade these applications, an on-bounds management system is usually best.
● A cloud-based management solution helps network operations teams align policies throughout the organization, reduce complication, and manage all security control points from a central dashboard. Information technology simplifies orchestrating and managing policies consistently from one spot to protect against the latest threats. With a centralized, deject-based application, you can streamline security management, deploy new devices faster with templates, and track all changes over time across your environs.
Step 3: Strengthen your security posture with integration. Your firewalling strategy should provide comprehensive coverage beyond all microperimeters and deliver protection and control across all continued devices and security solutions. Integrating security throughout your heterogeneous network, across cloud apps and services, corporate electronic mail, and all continued endpoints safeguards your business against the expanding threat landscape.
This step sets upwardly your security squad to block more threats, reply faster to advanced threats, and deliver automation across the network, to cloud apps, and endpoints.
Pace four: Finally, make sure your firewalling strategy incorporates ongoing avant-garde threat analysis to protect your concern avails and assist you stay ahead of new emerging threats. 1 of the easiest means is to cull a solution that automatically provides the latest threat information to your network through your firewall. Upwards- to-date intelligence and full visibility enable security teams to understand the latest vulnerabilities. And if a threat makes its way inside, you can place where and how it happened. Built-in next-generation IPS functionality automates risk rankings and bear upon flags to identify priorities and then the about critical assets and information can exist identified and prioritized. Security teams tin immediately take cosmetic action and remediate threats, staying focused on the most disquisitional assets versus being overwhelmed by the "noise," making SOC operations more secure.
It starts with the correct firewall as the foundation
Today's security teams need:
Ameliorate security backed by manufacture-leading threat intelligence to protect your complex network and find threats earlier and act faster.
A mode to efficiently ready, scale, and harmonize security policies across your network.
Visibility and reduced complication with unified direction and automation to accelerate security operations and meliorate their experience.
Networking and security that works together to maximize your existing investments. The correct solution will provide a deep gear up of integrations for comprehensive security that protects everything, everywhere.
The benefits of a firewalling strategy with Cisco Secure Firewall
Turn your entire network into an extension of your security architecture: By sharing common policy, intrusion prevention capabilities, and other cadre functions with Cisco Secure Firewall, switches and routers can perform security enforcement, tying the network infrastructure into a comprehensive security portfolio. Share threat intelligence across your architecture rapidly to correlate seemingly disconnected events, eliminate noise, and cease threats faster.
World-class security controls: Cisco Secure Firewall provides superior threat efficacy to protect your complex network against today'southward increasingly sophisticated attacks. Industry-leading, advanced threat intelligence helps your organization find new malware domains and malicious URLs likewise as unknown or undisclosed vulnerabilities to detect threats earlier and act faster. Built-in, side by side-generation IPS delivers comprehensive visibility with automated risk rankings and impact flags to place priorities for your security team, minimizing racket. Retrospective security keeps you informed and continually analyzes threats afterward initial detection to better identify sophisticated malware that may initially hide from detection.
Unified policy and threat visibility: Security teams can reach policy consistency and harmonization by standardizing and pushing security controls across every device — from network appliances to hosts and across the deject. Cisco's flexible and centralized management lets your team apply scalable controls to many devices quickly and hands to maintain consistent policies. Reduce complexity with unified direction and automated threat correlation beyond tightly integrated security functions, including application firewalling, NGIPS, and AMP. Streamline security policy and device management beyond extended networks and accelerate key security operations such as detection, investigation, and remediation.
Section 4: A future-set security solution
The way we piece of work has changed. Our businesses and networks have transformed, changing the rules of network security. These developments require us to re-think the firewall and embrace firewalling.
Cisco is driving innovation to address these trends with a security platform that delivers world-class security controls everywhere you need them with consistent security policies and visibility, backed past manufacture-leading threat intelligence. The latest generation of Cisco Secure Firewall forms the foundation of our portfolio of tightly integrated products.
Cisco'due south flagship deject direction solution – Cisco Defense force Orchestrator – delivers policy harmonization across a diverseness of Cisco security products.
Included in every Cisco security product is SecureX threat response , an automated threat response solution that reacts to new cyberattacks by automatically sharing and deploying countermeasures beyond the unabridged security compages.
Secure Endpoint delivers global threat intelligence, advanced sandboxing, and existent- time malware blocking. AMP continuously analyzes file activeness across your extended network for quick detection, containment, and removal of avant-garde malware.
Talos Threat Intelligence is a world-renowned team of full-fourth dimension threat researchers, data scientists, and engineers who collect data most existing and developing threats. Talos underpins the entire Cisco security ecosystem and delivers protection against attacks and malware. Talos provides visibility into the latest global threats, actionable intelligence on defence force and mitigation, and collective response to actively protect all Cisco customers.
SNORT Next-Generation Intrusion Prevention Organization (SNORT NGIPS) is an industry-leading, open- source NGIPS that performs traffic analysis, packet sniffing/logging, and protocol analysis. SNORT NGIPS leverages Talos threat intelligence to help the entire security community by sharing policies that protect against developing threats.
Adaptable, trusted access everywhere based on context is bachelor with Identity Services Engine (ISE). It provides intelligent, integrated protection through intent-based policy and compliance solutions.
Secure Access by Duo provides multi-factor authentication, endpoint visibility, adaptive authentication and policy enforcement with remote access and single sign-on to proactively secure access to applications.
Secure Network Analytics, Secure Workload, and Application Centric Infrastructure (ACI) work together, keeping tabs on your users wherever they get and their application workloads wherever they're located, using car- learning, behavioral modeling, network infrastructure telemetry, and partition to outsmart emerging threats.
Implement your future-ready firewalling strategy by investing in the Cisco security platform and Cisco Secure Firewall. You'll proceeds the strongest security posture available today and exist ready for tomorrow.
Department 5: Start building your future of the firewall today
Cisco brings networking leadership and cut-edge security technology together to evangelize the most secure compages always. Whether it's enhancing your network security by optimizing existing investments or transforming your routers into a firewall, Cisco continues to innovate.
Cisco Secure Firewall is network security designed for your digitally transforming business – from the company that built the network.
Larn more near Cisco Secure Firewall and get started on your future of firewalling today. And read more than about the latest trends shaping tomorrow's networks in the 2020 Global Networking Trends Report.
Source: https://www.cisco.com/c/en/us/products/collateral/security/firewalls/ngfw-futureoffirewalling-wp.html
0 Response to "Make Security Great Again Not by Building Firewalls"
Post a Comment